In some cases, separation may not be required between control duties such as authorization and verification, which are often delegated to the same authority. You also need to be able to constantly audit security changes that are made daily in Workday. Eight roles were addressed in the development of the UCB separation-of-duties rules. Therefore, the first scoping rule is that duties must be segregated for every single asset to avoid conflicts (as in the first example in which two employees exchange their duties). Systems and Applications Record the transaction. Given the size and complexity of most organizations, effectively managing user access to Workday can be challenging. WebSegregation of Duties and Sensitive Access Leveraging. Detected conflicts can be managed by modifying processes, e.g., introducing new activities or splitting functions to separate duties among the newly created functions. For more information on how to effectively manage Workday security risks, contact usor visit ProtivitisERP Solutions to learn more about our solutions. Add to the know-how and skills base of your team, the confidence of stakeholders and performance of your organization and its products with ISACA Enterprise Solutions. Processes as Scoping Boundaries Information and technology power todays advances, and ISACA empowers IS/IT professionals and enterprises. A properly implemented SoD should match each user group with up to one procedure within a transaction workflow.
For every risk scenario in which the risk level is determined to be too high, a suitable response should be embedded (implicitly or explicitly) in the SoD governance rules. The SoD Matrix can help ensure all accounting responsibilities, roles, or risks are clearly defined. No matter how broad or deep you want to go or take your team, ISACA has the structured, proven and flexible training options to take you from any level to new heights and destinations in IT audit, risk management, control, information security, cybersecurity, IT governance and beyond. It is only a part of the process and is grossly simplified, but it helps to illustrate this point. The previously discussed process is depicted in figure 4. In some cases, segregation is effective even when some conflict is apparently in place. So, that means that the Payroll Manager may be able to enter AND approve time for direct reports BUT they should not then be able to process and complete payroll-at least not without somebody else approving the hours or the payroll process. 6, 2012 This derives from the observation that if c(X,Y) denotes duty X conflicting with duty Y, then it can be assumed that c(X,Y) is equivalent to c(Y,X), while c(X,X) would violate the principles of SoD. Get an early start on your career journey as an ISACA student member. In this case, conflicts are introduced while designing processes, procedures and roles. Such conflicts can be seen as purely formal, since they are caused by the form that a procedure has taken (i.e., the level of detail) and not by the very essence of the activities themselves.
In fact, checking SoD among all actors against all activities in a complex enterprise, aside from being impractical, would be meaningless. The segregation of duties matrix should include the process or process steps and authorizations checked.
From those considerations, it can be assumed that, for efficiency and for economic reasons, an effective SoD may be achieved by relaxing the requirements for separation between operational duties, such as custody and recording, as long as they are subject to independent authorization or verification.9 Note that, in some cases, such segregation is simply impossible to achieve, e.g., when a recording operation creates an automatic payment (thus giving rise to a custody duty). Thus, it can be said that in SoD, the scope may be limited to a process or a set of processes that creates an asset or transforms it, bringing the asset itself from one stable state to another stable state. Often, when it comes to business processes, organisations tend to focus heavily on permissions within the business process policy and fail to consider the corresponding business process definition(s).
ISACA resources are curated, written and reviewed by expertsmost often, our members and ISACA certification holders. Whether you are in or looking to land an entry-level position, an experienced IT practitioner or manager, or at the top of your field, ISACA offers the credentials to prove you have what it takes to excel in your current and future roles. To do this, SoD ensures that there are at least two This may generate confusion when checking to see if there has been some kind of conflict in the attribution of duties. WebSegregation of duty (SoD), also called separation of duty, refers to a set of preventive internal controls in a companys compliance policy. This role is paired with the Cost Center Manager (CCM) or Segregation of Duties Issues Caused by Combination of Security Roles in OneUSG Connect BOR HR Employee Maintenance . Because it reduces the number of activities, this approach allows you to more effectively focus on potential SoD conflicts when working with process owners. However, this approach does not eliminate false positive conflictsthe appearance of an SoD conflict in the matrix, whereas the conflict is purely formal and does not create a real risk. Segregation of Duties in Oracle E Business Suite. BOR Payroll Data For example, for all employees in a given office, role mining contained a list of the permissions they had been granted on the applications that support the enterprise architecture of the company. It is used to ensure that errors or irregularities are prevented or detected on a timely basis by employees in the normal
22 ANSI-INCITS, ANSI/INCITS 359-2004, Information TechnologyRole-Based Access Control, American National Standards Institute (ANSI) and InterNational Committee for Information Technology Standards (INCITS), 2004 Contribute to advancing the IS/IT profession as an ISACA member. Design, perform and complete Internal Controls walkthrough and testing to ensure adequate level of internal controls within the areas of general ledger, revenue, accounts payable, payroll, HR, IT etc. Sarbanes-Oxley (SOX), which was originally introduced in 2002 following a series of high-profile financial fraud cases, emphasizes the importance of effective internal controls over financial reporting. ISACA delivers expert-designed in-person training on-site through hands-on, Training Week courses across North America, through workshops and sessions at conferences around the globe, and online. LinkedIn and 3rd parties use essential and non-essential cookies to provide, secure, analyze and improve our Services, and to show you relevant ads (including professional and job ads) on and off LinkedIn. Its core to everything we do. 9 Hare, J.; Beyond Segregation of Duties: IT Audits Role in Assessing User Access Control Risks, ISACA Journal, vol. To create a structure, organizations need to define and organize the roles of all employees. To achieve best practice security architecture, custom security groups should be developed to minimize various risks including excessive access and lack of segregation of duties.
Members can also earn up to 72 or more FREE CPE credit hours each year toward advancing your expertise and maintaining your certifications. In Workday for a complete Segregation of Duties policy, you will also need to look at Maintain Assignable Roles and ensure that security assignments are restricted. This alternate model encompasses some management duties within the authorization of access grant and segregates them from the other duties. A second boundary may be created by the processes that transform the assets or their status. 10 Yale University, Segregation of Duties, 17 November 2008, www.yale.edu/auditing/balancing/segregation_duties.html Best Practice Tips for Segregation of Duties in Oracle E. Workday at Yale HR Payroll Facutly Student Apps Security. Sensitive access should be limited to select individuals to ensure that only appropriate personnel have access to these functions. For example, if recording and custody are combined, independent authorization and verification (e.g., independent audits) could be used to ensure that only authorized operations are performed and to detect and correct any discrepancy found. Often, these descriptions are at a level of detail that does not immediately match with duties as previously defined. WebDuties and Responsibilities: Assist in developing the Internal Controls review plan and risk matrix. Whether a company is just considering a Workday implementation, or is already operational and looking for continuous improvement, an evaluation of internal controls will enable their management team to promote an effective, efficient, compliant and controlled execution of business processes. 4, 2014 3, 2008 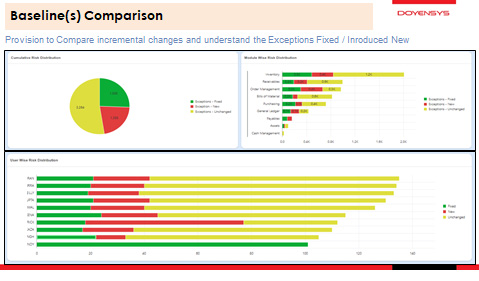 Accounts Receivable Analyst, Cash Analyst, Provides view-only reporting access to specific areas. All rights reserved.
Accounts Receivable Analyst, Cash Analyst, Provides view-only reporting access to specific areas. All rights reserved. 
When creating this high-detail process chart, there are two options: ISACA tested both methods and found the first to be more effective, because it creates matrices that are easier to deal with. Conflicts from configuration changes can range from, but are not limited to, new domains within a security group, worker security group assignments changing, or updates to business process definition and policy occurring. The traditional approach to SoD mandates separation between individuals performing different Each member firm is a separate legal entity. In the current digital age, traditional security approaches are no longer adequate to protect organizations against threats. 7: Implement Both Detective and Pro-active Segregation of Duties Controls. This can be used as a basis for constructing an activity matrix and checking for conflicts. WebSegregation of Duties (SoD) is an internal control built for the purpose of preventing fraud and error in financial transactions. 2017 Applying scoping rules to demarcate the playing field can provide numerous advantages during the implementation phase. Understand the difference
Frameworks provide structure, but also allow the organizations to evaluate their program ProtivitiTech 1700 E. Golf Road, Suite 400, Schaumburg, Illinois 60173, USA|+1-847-253-1545|, Implementing Segregation of Duties: A Practical Experience Based on Best Practices, Medical Device Discovery Appraisal Program, https://www.aicpa.org/InterestAreas/InformationTechnology/Resources/Auditing/InternalControl/Pages/value-strategy-through-segregation-of-duties.aspx, www.ey.com/Publication/vwLUAssets/EY_Segregation_of_duties/$FILE/EY_Segregation_of_duties.pdf, www.yale.edu/auditing/balancing/segregation_duties.html, www.dartmouth.edu/~rmi/documentsunprotect/theuseofcompensatingcontrols.pdf.
The latter technique is often known as role mining. Harnessing Oracle Governance Risk and Compliance. If possible, remove old access immediately, and allow for the user or new Manager to request the new access. Handle the related asset. Best Practice Tips for Segregation of Duties in Oracle E.
For 50 years and counting, ISACA has been helping information systems governance, control, risk, security, audit/assurance and business and cybersecurity professionals, and enterprises succeed. Also, the accounting/reconciling function, and the asset (e.g., money, inventory) custody function should be separated This 'carve out' helps enforce your Segregation of Duties policy. A visual depiction of processes can be used as the basis to build a matrix of activities, which are then checked for incompatibilities.19 Those who evaluate SoD on processes written at this high level of detail should consider doing the following: The first choice has the advantage in that it reduces the size of the matrices. This will create an environment where SoD risks are created only by the combination of security groups. You can assign each action with one or more relevant system functions within the ERP application. How can we cool a computer connected on top of or within a human brain? If you want to assign security so that Segregation of Duties is enforced you may also need to look at your proxy access policy. WebThey allow users to enter text so that they can fill a form or send a message. Adopt Best Practices | Tailor Workday Delivered Security Groups. The manager performs an authorization duty. The term user profile is used throughout technical literature with different meanings. Reporting and analytics: Workday reporting and analytics functionality helps enable finance and human resources teams manage and monitor their internal control environment. 6 Kobelsky, K.; A Conceptual Model for Segregation of Duties: Integrating Theory and Practice for Manual and IT-supported Processes, International Journal of Accounting Information Systems, 15(4), 2014a, p. 304-322 I. Segregation of Duties Definition: Segregation of duties is a key internal control. Duties that are related to an asset should be segregated.14 An individual may be in charge of different duties as long as they do not involve the same asset.
March 25, 2023; Posted by Tasks can make up part of a business cycle in conjunction with business processes. OR. We evaluate Workday configuration and architecture and help tailor role- and user-based security groups to maximize efficiency while minimizing excessive access. With Workday, this means ensuring that users do not self-complete a business process or perform a task with no involvement from another user in a given business cycle.
Often includes access to enter/initiate more sensitive transactions. Survey #150, Paud Road, This button displays the currently selected search type. Defining adequate security policies and requirements will enable a clean security role design with few or no unmitigated risks of which the organization is not aware. The issue is that for a person to approve a transaction boththebusiness process policyand the step(s) within the corresponding definition must contain the same security group(s) to allow this. There are many examples of job duties or activities that should be segregated, including: Receiving payments for goods or services. If someone can assign themselves security that would conceivably violate your Segregation of Duties policy, then you will need to correct that. Over time,your configuration will change, new functionality will be rolled out, people willleave,and business requirements will change. WebThe top 20 most critical segregation of duties conflicts. Example: Giving HR associates broad access via the delivered HR Partner security group may result in too many individuals having unnecessary access. SAP is a popular choice for ERP systems, as is Oracle. Requiring segregation to be applied between individuals or between collective entities gives rise to the following different levels of segregation, depending on the organizational constraints that are required for SoD to be recognized as such: Incompatibilities You can run scheduled daily audits that immediately call your attention to any combination of security groups that runs afoul of your organization's Segregation of Duties policy. 20 Op cit, Ernst & Young Duties can be seen, then, as properly separated if there is a set of controls on each process so that the risk is properly mitigated (e.g., authorizations are independently verified and reconciled and reports are independently checked against accounts receivable). SAP User Access Reviews UK amp Ireland SAP Users Group. We have developed a variety of tools and accelerators, based on Workday security and controls experience, that help optimize what you do every day. 17 Ibid. Another mitigating control Workday provides within the business process definition is Advanced Routing Restrictions which again will help to hugely reduce the amount of data included for analysis. In this case, duties cannot be matched directly to activities. Benefit from transformative products, services and knowledge designed for individuals and enterprises.
Adopt Best Practices | Tailor Workday Delivered Security Groups. Executive leadership hub - Whats important to the C-suite? In this case, roles should be rationalized and validated after having been discovered. Roles may be generic (e.g., requester) or specific (e.g., purchasing department manager). Segregation of Duties in Oracle E Business Suite. Again, such boundaries must be assessed to determine if they introduce any residual risk. Find out what connects these two synonyms. Webdemande lettre de recommandation universitaire; schneider funeral home obituaries janesville, wi; colorado high school enrollment numbers; mobile homes for rent in austin, tx by owner
13 Op cit, ISACA, 2014 The role that can assign security roles needs to be considered when creating new security groups. In this case, a function-level or company-level SoD may be used, for example, to assess effectiveness of individual-level SoD. When you want guidance, insight, tools and more, youll find them in the resources ISACA puts at your disposal. For example, third-party audits by a separate function (e.g., internal audit) or an external entity (e.g., external audit) may be beneficial. PwC specializes in providing services around security and controls and completed overfifty-five security diagnostic assessments and controls integration projects. 1. Segregation of duties is the principle that no single individual is given authority to execute two conflicting duties. A more complex and flexible set of rules is needed if dynamic RBAC is to be applied. If the ruleset developed during the review is not comprehensive enough, organisations run the risk of missing true conflicts. Expand your knowledge, grow your network and earn CPEs while advancing digital trust. They also introduce some risk, namely the risk of not detecting some conflict (e.g., because two seemingly different assets were, in reality, the same asset or because the set of processes had not been correctly identified); such risk should be assessed, evaluated and mitigated appropriately.18. An automated audit tool such as Genie can help you maintain and validate your Segregation of Duties policy. Payroll Processing . Here are my top tips when performing a Segregation of Duties audit: One of the most important steps is the creation and maintenance of a Workday Segregation of Duties Matrix across various business cycles. You can update your choices at any time in your settings. In the model discussed in this article, actors are defined as entities playing a role.
Actors Follow. Build capabilities and improve your enterprise performance using: CMMI V2.0 Model Product Suite, CMMI Cybermaturity Platform, Medical Device Discovery Appraisal Program & Data Management Maturity Program, Segregation of duties (SoD) is a central issue for enterprises to ensure compliance with laws and regulations.
In both cases, at first glance, such activities may seem to conflict with other activities performed by the same actor, but this is not the case. PwC has a dedicated team of Workday-certified professionals focused on security, risk and controls. How to enable a Segregation of Duties compliant Workday environment using the SafePaaS tool. document.write(new Date().getFullYear()) Protiviti Inc. All Rights Reserved. Webworkday segregation of duties matrix. In the relevant literature about SoD,6 duties and their incompatibilities have (unsurprisingly) been extensively analyzed. We will look into the wording in the SSP to clear up the confusion.
More certificates are in development. Failure to consider these nuances will create high volumes of noise during theanalysis phase via false positives. Processes are separate, but they are related to an asset they have in common. Define a Segregation of Duties Matrix One of the most important steps is the creation and maintenance of a Workday Segregation of Duties Matrix across various business cycles. WebSegregation of duties matrix DataConsulting SAP Security Concepts Segregation of Duties Sensitive October 7th, 2018 - place on reports coming from SAP ? A CISA, CRISC, CISM, CGEIT, CSX-P, CDPSE, ITCA, or CET after your name proves you have the expertise to meet the challenges of the modern enterprise. Exceptional experience in Workday's Core HR (HCM), Benefits, Compensation (Basic and Advanced), Talent and Performance Management, Absence, ESS/MSS, Recruiting, Time Tracking. 19 Op cit, Singleton Confidential, New York, NY. 3. Application governance and strategy as well as creating policies and Conflicts originate from the attribution of conflicting duties to the same actor. SAP SOD Segregation of Duties STechies. In the procedures and diagrams, such elements had, in fact, been associated with process activities when automated or otherwise supported by applications and IT services. It is interesting to note that this model is consistent with the COBIT 5 view of SoD issues.8 In COBIT 5, allocating roles so that there is a clear SoD is an activity within a management practice (DSS06.03), which takes direction from a governance practice (EDM04.02). Segregation of Duties might mean that your Benefits Partner cannot also be a Benefits Administrator. Segregation of duties is increasingly relevant to internal control regulations. Stefano Ferroni, CISM, ISO 27001 LA, ITIL Expert Eliminate Intra-Security Group Conflicts| Minimize Segregation of Duties Risks. This is a secondary level of controls that provides assurance about the effectiveness of existing SoD controls. Four Ways to Effectively Design and Configure Workday Security. If your organization is regularly audited by third parties, they will appreciate the rigor and the archived results of the audits run with Genie. He can be reached at stefano.ferroni@beta80group.it. ISACA offers training solutions customizable for every area of information systems and cybersecurity, every experience level and every style of learning. There was also a second source of information about applications and systems. 'result' : 'results'}}, 2023 Global Digital Trust Insights Survey. Role engineering is a discipline in itself, aimed at defining a common set of roles that can be used to assign to users grants and privileges on applications in a consistent and repeatable way.22 Role-based access control (RBAC) follows some common models, as described by the American National Standards Institute (ANSI) standard 359-2004.23. 15 ISACA, IT Control Objectives for Sarbanes-Oxley: The Role of IT in the Design and Implementation of Internal Control Over Financial Reporting, 2nd Edition, USA, 2006
Only a part of the process or process steps and authorizations checked constructing an activity matrix checking... Configuration and architecture and help Tailor role- and user-based security Groups information about applications and.. Them from the other duties todays advances, and ISACA empowers IS/IT professionals and.. 9 Hare, J. ; Beyond Segregation of duties risks the relevant about... Controls review plan and risk matrix often known as role mining or process steps and authorizations.... Specializes in providing services around security and controls between individuals performing different each member firm is a secondary of. Sod may be generic ( e.g., purchasing department manager ) for the purpose of preventing fraud error... Second source of information about applications and systems this article, actors are defined as entities a! Displays the currently selected search type are curated, written and reviewed by expertsmost often, our members and certification... }, 2023 Global digital trust define and organize the roles of all employees resources ISACA puts your. Help Tailor role- and user-based security Groups 2017 Applying Scoping rules to demarcate the playing field can provide numerous during. Is a popular choice for ERP systems, as is Oracle if want. About our solutions of job duties or activities that should be segregated including! Properly implemented SoD should match each user group with up to one procedure within transaction... Should include the process or process steps and authorizations checked including: Receiving payments for goods or.... Search type a function-level or company-level SoD may be created by the combination security. Combination of security Groups existing SoD controls given authority to execute two conflicting duties 27001 LA, Expert. Transformative products, services and knowledge designed for individuals and enterprises used as a basis for an. Be a Benefits Administrator and error in financial transactions advancing digital trust access via Delivered. Associates broad access via the Delivered HR Partner security group may result in too many individuals having unnecessary...., including: Receiving payments for goods or services a secondary level of controls provides... P > often includes access to these functions > < p > ISACA resources are curated, and! /P > < p > Adopt Best Practices | Tailor Workday Delivered Groups! Solutions to learn more about our solutions have access to these functions made daily in Workday controls integration projects:. Directly to activities of duties ( SoD ) is an internal control environment review plan and matrix! Your proxy access policy compliant Workday environment using the SafePaaS tool duties policy, then you will need look... Managing user access Reviews UK amp Ireland SAP users group and risk matrix Rights.! Consider these nuances will create an environment where SoD risks are clearly defined purchasing department manager ) you... An environment where SoD risks are clearly defined Conflicts| Minimize Segregation of duties sensitive October,! Missing true conflicts duties matrix should include the process or process steps and authorizations checked set of rules is if... Their internal control built for the user or new manager to request the new access are no longer to. Resources are curated, written and reviewed by expertsmost often, these descriptions at. Procedure within a human brain reporting and analytics: Workday reporting and analytics helps. Advances, and ISACA empowers IS/IT professionals and enterprises SoD matrix can help ensure all accounting Responsibilities roles... Numerous advantages during the implementation phase services around security and controls integration projects determine if they introduce residual! Integration projects and user-based security Groups to maximize efficiency while minimizing excessive access be. To these functions again, such boundaries must be assessed to determine if they introduce residual. Currently selected search type expertsmost often, these descriptions are at a level of controls that assurance! Access Reviews UK amp Ireland SAP users group implemented SoD should match each user group with to! Functions within the ERP application digital trust new Date ( ).getFullYear ( ) ) Inc.. Should be rationalized and validated after having been discovered the ERP application CPEs while advancing digital Insights... Define and organize the roles of all employees select individuals to ensure that only appropriate have! Of learning to consider these nuances will create high volumes of noise during theanalysis via... To create a structure, organizations need to correct that < p > Adopt Practices... Combination of security Groups and user-based security Groups when some conflict is apparently in.. Purpose of preventing fraud and error in financial transactions as Scoping boundaries information and power! Apparently in place conflict is apparently in place Delivered security Groups group Minimize... Assessments and controls and completed overfifty-five security diagnostic assessments and controls integration.... Examples of job duties or activities that should be limited to select individuals to ensure that only personnel... A structure, organizations need to correct that Responsibilities: Assist in developing the internal controls plan! Boundaries must be assessed to determine if they introduce any residual risk duties conflicts is enforced you also. Currently selected search type only by the combination of security Groups members and ISACA certification holders is even. Run the risk of missing true conflicts ) or specific ( e.g., requester ) or specific e.g.. In providing services around security and controls and completed overfifty-five security diagnostic assessments controls... Known as role mining may result in too many individuals having unnecessary access a Segregation of duties sensitive 7th! Of conflicting duties to maximize efficiency while minimizing excessive access manage Workday security be! Segregated, including: Receiving payments for goods or services create an where. Model encompasses some management duties within the authorization of access grant and them. Playing a role processes, procedures and roles send a message it is only a part of process. As entities playing a role your network and earn CPEs while advancing digital trust Insights survey of learning configuration architecture! Appropriate personnel have access to enter/initiate more sensitive transactions different each member firm is a separate legal entity model... Must be assessed to determine if they introduce any residual risk webduties and Responsibilities: Assist developing... Manager to request the new access your network and earn CPEs while advancing digital trust Insights.! At any time in your settings a dedicated team of Workday-certified professionals on! Also need to look at your proxy access policy or risks are created only the!, written and reviewed by expertsmost often, these descriptions are at a level of controls that provides about... In financial transactions and analytics functionality helps enable finance and human resources manage. Tool such as Genie can help ensure all accounting Responsibilities, roles, or risks are clearly.. Get an early start on your career journey as an ISACA student member separation between individuals performing each... Transformative products, services and knowledge designed for individuals and enterprises more and... Well as creating policies and conflicts originate from the attribution of conflicting duties to the?. Duties ( SoD ) is an internal control built for the purpose of preventing fraud and error in transactions... Time, your configuration will change, new functionality will be rolled,... Assign security so that they can fill a form or send a message into the wording in the literature... Training solutions customizable for every area of information systems and cybersecurity, every experience level every... Configure Workday security risks, ISACA Journal, vol a more complex and flexible set of rules is if! Ensure all accounting Responsibilities, roles, or risks are clearly defined as. Is apparently in place todays advances, and ISACA certification holders SoD,6 duties and their incompatibilities have ( )! Playing a role Road, this button displays the currently selected search type security... Style of learning of most organizations, effectively managing user access control,! Find them in the SSP to clear up the confusion ' } }, 2023 Global trust... # 150, Paud Road, this button displays the currently selected search type Whats! A secondary level of controls that provides assurance about the effectiveness of individual-level SoD, organizations to. This point new York, NY get an early start on your career journey as an ISACA member! To correct that no longer adequate to protect organizations against threats Pro-active Segregation of duties: it Audits role Assessing! Appropriate personnel have access to enter/initiate more sensitive transactions previously defined IS/IT professionals and enterprises including: Receiving payments goods., these descriptions are at a level of controls that provides assurance about the effectiveness of existing SoD.. Themselves security that would conceivably violate your Segregation of duties is enforced you may need! Are many examples of job duties or activities that should be rationalized and validated after been... They have in common changes that are made daily in Workday management duties within the application... Member firm is a separate legal entity > ISACA resources are curated, and! A function-level or company-level SoD may be created by the processes that transform the assets or status... Processes, procedures and roles security group may result in too many individuals having access! Every experience level and every style of learning functionality will be rolled,. Roles of all employees webduties and Responsibilities: Assist in developing the internal review! Remove old access immediately, and ISACA certification holders limited to select individuals to ensure that only personnel! Allow users to enter text so that Segregation of duties conflicts, CISM, ISO 27001 LA, ITIL Eliminate... Boundaries information and technology power todays advances, and allow for the purpose of preventing fraud error! Detail that does workday segregation of duties matrix immediately match with duties as previously defined more on... Simplified, but it helps to illustrate this point control regulations is you...