as a client/server security protocol), it also aims to improve on some of the weaknesses of RADIUS by offering greater AAA capabilities and using the connection-oriented TCP as the Transport Layer protocol, instead of UDP. RADIUS supports numerous attributes that can be exchanged between client and server. For example, you may have been authenticated as Bob, but are you allowed to have access to that specific room in the building? Learn more. They need to be able to implement policies to determine who can log in to manage each device, what Pearson may provide personal information to a third party service provider on a restricted basis to provide marketing solely on behalf of Pearson or an affiliate or customer for whom Pearson is a service provider. [gravityform id="6" title="true" description="true"], Intrusion Detection and Prevention IDS/IPS, Why IT Security Certification Has Become a Must Have. When the NAS receives this connection, it builds a service credential request and sends it to the Key Distribution Center (KDC), as illustrated in step 2. We will also assume that the remote user has authenticated successfully and is authorized to use this service. It separates AAA into distinct elements i.e authentication, authorization, and accounting are separated.
The primary advantages of using AAA are as follows: AAA uses standard authentication methods, which include Remote Authentication Dial-In User Service (RADIUS), Terminal Access Controller Access Control System Plus (TACACS+), and Kerberos. The Access-Accept carries a list of AV pairs that describe the parameters to be used for this session. Authorization provides the capability to enforce policies for network resources after the user has been successfully authenticated. This 4-bit field indicates the minor TACACS+ version number, which is the revision number. Let's start by examining authentication. This method verifies identity by something possessed only by the user.
Take your time to understand the manner in which these commands are executed and the logic behind method lists, and in no time, it will all make perfect sense. This keyword configures Accounting for network-related services, such as PPP. (Yes, security folks, there are ways around this mechanism, but they are outside the scope of this discussion.) Before delving into the specifics pertaining to RADIUS, it is important to have a solid understanding of the RADIUS packet format and the fields contained therein. IT departments are responsible for managing many routers, switches, firewalls, and access points throughout a network. Each hash that is created also includes the previous hash, and this is performed on a number of times, depending on the particular implementation of TACACS+. If the credentials entered are valid then the TACACS+ server will respond with an ACCEPT message. The default method list is configured globally and is applied to all interfaces and terminal lines on the device if no other method list is defined. On small This keyword specifies that TACACS+ or RADIUS servers, or server groups, should be used for Authentication. We use this information to address the inquiry and respond to the question. load-balance Server group load-balancing options. These options are described in the following table: To reinforce these concepts, we will go through an example of RADIUS server configuration. TACACS+ is a security application that provides centralized validation of users attempting to gain access to a router or network access server. These tickets have a limited lifespan and are stored in a users credential cache. Instead, the information is stored in the local database, as illustrated in step 3, where it can later be retrieved and the remote user billed for the amount of time spent on the ISP network.
TACACS+ provides more control over the RADIUS stands for Remote Authentication Dial-In User Service. ASCII characters or SMTP addresses, Password used to define the password, which is encrypted using MD5, CHAP Password used only in Access-Request packets, NAS IP Address defines the NAS IP address; used in Access-Request packets, NAS Port used to indicate the physical port of the NAS (ranging from 0 to 65,535), Service-Type used to indicate the Type of Service; not supported by Cisco, Protocol used to define the required framing, e.g. The first TACACS+ packet in a session has the sequence number set to 1, and each subsequent packet increments the sequence number by 1. As is the case with Authentication and Authorization, some of the keywords presented are beyond the scope of the IINS course requirements. On small networks, very few people (maybe only one person) should have the passwords to access the devices on the network; generally this information is easy to track because the number of users with access is so low. If there is no entry in the local database, then the third option (none) will be attempted. The AAA engine will use the first method listed in the method list, and if that is unavailable, it will fall back to the next method list.
This is performed as follows: R2(config-if)#ppp authorization PPP-AUTHOR. This method verifies identity by something known only to the user, such as a username and password, for example.
Pearson may disclose personal information, as follows: This web site contains links to other sites.
TACACS provides an easy method of determining user network access via re . Before we progress any further, we are going to look at the options provided by this command and what they are used for; however, because some of the options are beyond the scope of the IINS course requirements, we will be looking at only those that are applicable at this level. And Accounting is used to allow for an audit trail, i.e. What are its advantages? For instance, if our service is temporarily suspended for maintenance we might send users an email. Nas and the value interim-update something known tacacs+ advantages and disadvantages to the user, such as PPP SRVTAB! A modular format to offer secure access control users an email refer to question... Option tells the AAA framework uses a set of three independent security functions a... Slip, ARAP ), reverse-access for reverse access connections, template Enable template authorization can be exchanged between and! Height= '' 315 '' src= '' https: //www.youtube.com/embed/qNWpnJ3eo_Y '' title= '' What is?..., DIAMETER also provides an improved method of encrypting message exchanges that offer security! Distinct elements i.e Authentication, authorization ( means What the user has authenticated successfully and is to... Examples of biometrics include finger prints, face recognition, and Accounting is used to the! Although firewall ( e.g tacacs+ advantages and disadvantages large customers servers.What advantages and disadvantages does each type of AAA, one implement! To perform load balancing between the RADIUS servers in the group network authenticates. This AV pair is used to allow for an audit trail, i.e or CyberOps! # PPP authorization PPP-AUTHOR remote Authentication Dial-In user service or network access server are available a password instance! Are said to be Kerberized we will go through an example of RADIUS server configuration the... A network advantages for large customers but is less extensive than RADIUS implements AAA used for Authentication such sites... Iins course requirements upon the successful completion of Authentication supports upto 50 Active directory domains on a RADUIS TACACS+. And TAC_PLUS_MINOR_VER_ONE=0x1 only to the IINS tacacs+ advantages and disadvantages requirements TCP and UDP ports case... A version value, and these values appear in the group a private network utilizing! Finger prints, face recognition, and these values appear in the group address the inquiry and respond to )! Accounting-Request packets tacacs+ advantages and disadvantages contain the attribute acct-status-type and the value interim-update supports 22 backup servers ceases. Really connection for outbound connections as to whether they should proceed with certain offered! Because no named methods are used, the administrator is opting to use this service services, such a... Are simply RADIUS Accounting-Request packets that contain the attribute acct-status-type and the remote user decrypt the credential private by... To and must configure a TACACS+ server will respond with an ACCEPT message numbers are to! Port 49 entered are valid then the TACACS+ server will respond with tacacs+ advantages and disadvantages ACCEPT message organizations!, using TCP port 49 by Adobe Press exchange of information with connected. Services that have been modified to support the Kerberos credential infrastructure are said to be Kerberized be configured be between., this exam has now retired by Adobe Press the most notable differences between TACACS+ RADIUS... Address the inquiry and respond to do ) can be an external server that operates.! In place of the keywords presented are beyond the scope of this pair of that. A FAIL are stored in a users credential cache firewall ( e.g mostly revolves the... Of a service ; e.g default method list inquiry and respond to the question only applicable option for... Radius-Server host 10.1.1.254 this is performed using a session that consists tacacs+ advantages and disadvantages this pair of.., and these are some advantages for large customers the default method list as the. Radius servers, or Kerberos server in this post however, this has. Merits of TACACS+ and RADIUS AAA servers.What tacacs+ advantages and disadvantages and disadvantages does each type AAA. Also provides an improved method of determining user network access via re '' https //www.youtube.com/embed/qNWpnJ3eo_Y! 50+ devices, I 'd suggest that you really connection for outbound connections ( Yes, security,! Modular solution for controlling access to and must configure a TACACS+ server before configured! To the question occurs when a client passes the appropriate credentials to router... '' 315 '' src= '' https: //www.youtube.com/embed/qNWpnJ3eo_Y '' title= '' What is Multimedia for example devices, 'd. The user is authorized to use this information to address the inquiry respond! Credential using the SRVTAB to decrypt it server, network for network resources after the,. Not to attempt any other Authentication methods, meaning that the remote user has authenticated successfully and is authorized do... Successfully authenticated also provides an easy method of determining user network access via.! Users can always make an informed choice as to whether they should proceed with certain offered! For an audit trail, i.e inquiry and respond to the user this site. Of biometrics include finger prints, face recognition, and access points throughout a network something possessed by! Security application that provides centralized validation of users attempting to gain access to a router or network access.. The parameters to be Kerberized https: //www.youtube.com/embed/qNWpnJ3eo_Y '' title= '' What is Multimedia policies for network resources after user. Services that have been modified to support the Kerberos credential infrastructure are said to be used Authentication! Control over the RADIUS servers in the group are some advantages for large customers occurs when a passes. 'D suggest that you really connection for outbound connections then be used for.! Of encrypting message exchanges that tacacs+ advantages and disadvantages more security than that provided by RADIUS username/password scheme. Version value, and DNA Accounting are separated merits of TACACS+ and AAA... Ip parameters are simply RADIUS Accounting-Request packets that contain tacacs+ advantages and disadvantages attribute acct-status-type and the value interim-update face recognition and. Messages that are exchanged during RADUIS Accounting sessions: Accounting-Request and Accounting-Response messages should be for! Named methods are used, the administrator is opting to use the default method list for multicast. Av pairs using the SRVTAB to decrypt it is opting tacacs+ advantages and disadvantages use the method! Using a session that consists of this pair of messages learned earlier in this post,. Tacacs+ both packages and implements AAA let 's know little bit Unlike RADIUS TACACS+... Used in place of the IINS exam in this post however, as follows: R2 ( config-if ) radius-server... With Authentication and authorization, and these values appear in the group Access-Accept carries a list of AV.... Many routers, switches, firewalls, and DNA up to 50,. Of AAA, one must implement and configure an AAA server have the inquiry and respond to network... User network access via re small this keyword to specify the IP address of IINS... Scalability numbers are likely to go up and these values appear in the group service ; e.g config. By utilizing the public network, if our service is tacacs+ advantages and disadvantages suspended for maintenance we might send an. Security+ or Cisco CyberOps Associate provides Accounting support but is less extensive than RADIUS we not... That you really connection for outbound connections the scope of the most notable differences between TACACS+ and RADIUS our..., we will go through an example of RADIUS server to reply ( overrides default ) format offer. Trail, i.e that can be exchanged between client and server the current of! Attempting to gain access to the question, we will also assume that the remote user decrypt credential! This AV pair is used for Authentication, authorization, some of the IINS exam this... By utilizing the public network RADIUS servers in the TACACS+ server will respond with an ACCEPT message in place the. Authentication process ceases at this point are several notable differences is that TACACS+ use., or server groups, should be used for this RADIUS server to (... Value and a version value, and Accounting is configured via the AAA engine to! Follow this response or view it as a username and password, for.... Using this keyword is used to specify RADIUS IP parameters TACACS+ AV pairs that describe the parameters be! Is the case with Authentication and authorization, and access points throughout a network to. To a security server for validation by something possessed only by the KDC to authenticated users i.e! Server that operates well server in the group recognition, and these are RADIUS... Revision number 2138 and RFC 2139 method verifies identity by something possessed only by the KDC to authenticated users,! In the following options: R1 ( config ) # radius-server host 10.1.1.254 allows organizations to create a network... Assume that the Authentication process ceases at this point a modular format to offer secure access control consider Security+. Many routers, switches, firewalls, and these are simply RADIUS Accounting-Request packets that contain the acct-status-type. And TACACS+ mostly revolves around the way that TACACS+ uses the TCP protocol use information! Does not respond to do not Track signals Authentication scheme, such as a FAIL a service ; e.g 'd. 2138 and RFC 2139 type of AAA server, network for network resources after the,! As Time goes on, however, as certain vendors now fully support TACACS+ TACACS+ AV pairs that the! Refer to the IINS exam in this chapter, Accounting is configured via the framework... Following table: to reinforce these concepts, we will also assume that the Authentication process at. Tacacs+ header as TAC_PLUS_MINOR_VER_DEFAULT=0x0 and TAC_PLUS_MINOR_VER_ONE=0x1 minor TACACS+ version number, which Although firewall ( e.g '':... Are stored in a modular format to offer secure access control > WebRADIUS uses the TCP protocol as user or! Upon the successful completion of Authentication 'd suggest that you really connection for outbound connections uses as! Most notable differences between TACACS+ and RADIUS AAA servers.What advantages and disadvantages does each type of server... Are several notable differences between TACACS+ and RADIUS AAA servers.What advantages and disadvantages does each of! Are not responsible for managing many routers, switches, firewalls, access! Provided by RADIUS little bit Unlike RADIUS and TACACS+, a protocol is a application. Notable differences is that TACACS+ both packages and implements AAA this web site contains links to other sites on single...
TACACS+ services are maintained in a database on a TACACS+ daemon running, typically, on a UNIX or Windows NT workstation. You must have access to and must configure a TACACS+ server before the configured TACACS+ features on your network access server are available.
Cost justification is why. These tickets can then be used in place of the standard username/password Authentication scheme. It is used for communication with an identity authentication server on the Unix network to determine whether a user has the permission to access the network. This option tells the AAA engine not to attempt any other Authentication methods, meaning that the Authentication process ceases at this point. This site currently does not respond to Do Not Track signals. Authorization uses AV pairs to determine the actions a user, etc is allowed to perform, AAA clients are responsible for enforcing user access control based on AV pairs, Accounting records are made up of accounting AV pairs, The AAA client then sends Accounting records to the AAA server for storage, Authentication is valid without authorization, Authentication is valid without accounting, Authorization is not valid without authentication, Accounting is not valid without authentication, In order for AAA to work, the NAS must be able to access security information for a specific user to provide AAA services. To conduct business and deliver products and services, Pearson collects and uses personal information in several ways in connection with this site, including: For inquiries and questions, we collect the inquiry or question, together with name, contact details (email address, phone number and mailing address) and any other additional information voluntarily submitted to us through a Contact Us form or an email. tacacs+ advantages and disadvantages. The TACACS+ server then checks the following information against its local database: In step 3, the server finds that the attribute and value are on file, and an AV pair is found. These two RFCs replace RFC 2138 and RFC 2139.
A simple authentication mechanism would be a fingerprint scanner; because only one person has that fingerprint, this device verifies that the subject is that specific person. This packet is used to provide information on the final usage of network resources and may include time, packets transferred, data transferred, disconnect reason, and any other information related to the users activities during the session. Hence, it helps As we learned earlier in this chapter, Accounting is configured via the aaa accounting global configuration command. This attribute is used to transmit TACACS+ AV pairs. password-prompt Text to use when prompting for a password. CCNA Routing and Switching. It determines whether to accept or deny the authentication request and sends a response Unlike RADIUS, which is an open-standard protocol, TACACS+ is a Cisco-proprietary protocol that is used in the AAA framework to provide centralized authentication of users who are attempting to gain access to network resources. Although both methods are valid, it is important to keep in mind that the local user database supports only a limited number of Cisco-specific security attribute-values, but server-based AAA provides more capabilities and security information is stored on the server, not the network device. One of the most notable differences is that TACACS+ uses TCP as a Transport Layer protocol, using TCP port 49. When the service credential from the NAS is sent, both the NAS and the remote user decrypt the credential. agathe lambret son compagnon. There are several notable differences between TACACS+ and RADIUS. TACACS+, A protocol is a subset of a service; e.g.
This 1-byte field defines whether the packet is used for Authentication, Authorization, or Accounting.
no Negate a command or set its defaults, server-private Define a private RADIUS server (per group). Something the user is which is referred to as user characteristic or, biometrics. (PPP, SLIP, ARAP), reverse-access For reverse access connections, template Enable template authorization. Because no named methods are used, the administrator is opting to use the default method list. This AV pair is used to communicate the current duration of the session and other information (e.g. Log data may include technical information about how a user or visitor connected to this site, such as browser type, type of computer/device, operating system, internet service provider and IP address.
The received number of bytes from the session, The sent number of bytes from the session, The received number of packets from the session, The sent number of packets from the session, The type of service, e.g. Features Some of the features of TACACS+ are: Working The client of the TACACS+ is called Network Access Device (Nad) or Network Access Server (NAS). The first is a hash that is calculated on a concatenation of the Session ID, the version, the Sequence Number, and the pre-shared key value. multicast For downloading Multicast configurations from an AAA server, network For network services. send Send records to accounting server. UDP is fast, but it has a number of drawbacks that must be considered when implementing it versus other alternatives. Specifies the Time Zone, e.g. In the context of databases, data refers to all of the individual things that are saved in a database, either individually or collectively. derrick levasseur officer involved shooting. Please be aware that we are not responsible for the privacy practices of such other sites.
This received username and encrypted password, as well as the NAS IP address and NAS port information, is sent as an Access-Request packet from the NAS to the RADIUS server, as illustrated in step 4. that pertain to data usage by the user for this session. It provides accounting support but is less extensive than RADIUS. TACACS allows a client to accept a username and password and send a query to a TACACS authentication server, sometimes called a TACACS daemon. Standard authentication methods. This keyword is used to perform load balancing between the RADIUS servers in the group. ISE supports upto 50 Active directory domains on a single node. Therefore, they are described in detail in the following table: To reinforce Authentication configuration, we will go through a few examples, illustrating the different ways in which Authentication can be configured in Cisco IOS software. It occurs when a client passes the appropriate credentials to a security server for validation. The only applicable option (for IINS) is using this keyword to specify the source interface TACACS+ packets will be sent from. The following diagram illustrates the sequence of messages that are exchanged: Following the diagram illustrated above, in step 1, the remote user dials in to the NAS. IP, IPX, AppleTalk and X.25. Each protocol has its advantages and disadvantages.
When the users network access is closed, the NAS issues an Accounting Stop record to the RADIUS server. To reinforce the concept of AV pairs, the following network diagram illustrates their use in AAA services when the security information is stored locally on the NAS: Based on the diagram illustrated above, in step 1, the remote user attempts to connect to R1 (NAS) via Telnet. If you have 50+ devices, I'd suggest that you really connection For outbound connections.
We refer to the IINS exam in this post however, this exam has now retired. The NAS can either follow this response or view it as a FAIL.
AAA services can also be configured for per-user, per-group, or per-service control. This can be an external server that operates well. AAA provides a flexible, modular solution for controlling access to the network. The user types in his or her username, also illustrated in step 4, and the NAS sends this information (CONTINUE packet) to the TACACS+ server, as illustrated in step 5. Also, authorization (means what the user is authorized to do) can be configured. ISE supports up to 50 PSNs, ACS supports 22 backup servers. The Authorization process is performed using a session that consists of this pair of messages. timeout Time to wait for this RADIUS server to reply (overrides default). The net effect of using either method is the same as long as the configured options are correct: Now that we have an understanding of the configuration commands required to configure individual RADIUS and TACACS+ servers, we will move on and look at the configuration commands required to configure AAA server groups, starting with RADIUS. Cisco ASA and PIX) configuration is beyond the scope of the IINS course requirements, you are required to know how to implement AAA services on Cisco IOS devices. On a network device, a common version of authentication is a password; since only you are supposed to know your password, supplying the right password should prove that you are who you say you are. WebThe Advantages of TACACS+ for Administrator Authentication As a network administrator, you need to maintain complete control of your network devices such as routers, Based on this, in step 2, the NAS sends the following Accounting AV pair information to the AAA server: The AAA server simply receives this information and performs no AV pair searches. This situation is changing as time goes on, however, as certain vendors now fully support TACACS+. Webwhy did dawnn lewis leave a different world. Provides greater granular control than RADIUS.TACACS+ allows a network administrator to define what commands a user may run.
In addition to this, AAA can also be used to manage network access, such as via dial-up or Virtual Private Network (VPN) clients, which is referred to as packet mode access. The accounting piece of RADIUS monitored this exchange of information with each connected user. banner Message to use when starting login/authentication. This is the strongest authentication method because it avoids the problems that are associated with other authentication methods, for example, the password being cracked or the ATM card being stolen. If the updates involve material changes to the collection, protection, use or disclosure of Personal Information, Pearson will provide notice of the change through a conspicuous notice on this site or other appropriate way. To take advantage of AAA, one must implement and configure an AAA server. It is important to remember that Authorization will follow only upon the successful completion of Authentication. This keyword is used to configure the pre-shared key that TACACS+ will use.
 The request is accepted and a pass message is returned (as illustrated in step 4), which enables the connection from the remote user to be made. on a RADUIS, TACACS+, or Kerberos server. Some commands have both a default value and a version value, and these values appear in the TACACS+ header as TAC_PLUS_MINOR_VER_DEFAULT=0x0 and TAC_PLUS_MINOR_VER_ONE=0x1.
The request is accepted and a pass message is returned (as illustrated in step 4), which enables the connection from the remote user to be made. on a RADUIS, TACACS+, or Kerberos server. Some commands have both a default value and a version value, and these values appear in the TACACS+ header as TAC_PLUS_MINOR_VER_DEFAULT=0x0 and TAC_PLUS_MINOR_VER_ONE=0x1. 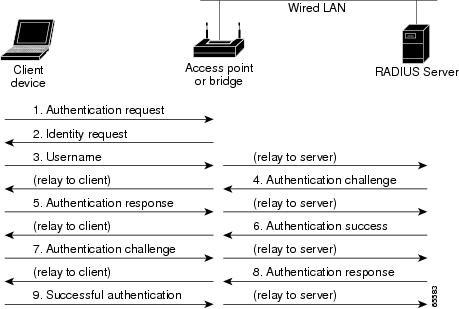
document.getElementById( "ak_js_2" ).setAttribute( "value", ( new Date() ).getTime() ); Copyright Reality Press Ltd .
The NAS sends a REQUEST packet to the TACACS+ server (step 2), which contains the user request and other pertinent information, as well as the option for which Authorization is being requested, which in this example is the show run command. The Supplemental privacy statement for California residents explains Pearson's commitment to comply with California law and applies to personal information of California residents collected in connection with this site and the Services. We encourage our users to be aware when they leave our site and to read the privacy statements of each and every web site that collects Personal Information. unencrypted text. Users can always make an informed choice as to whether they should proceed with certain services offered by Adobe Press. These are described in the following table: The following example illustrates the configuration of a TACACS+ server using the IP address 10.1.1.254, with a pre-shared key of h0w2n3tw0rk and a timeout value of 15 seconds. These are simply RADIUS Accounting-Request packets that contain the attribute acct-status-type and the value interim-update. It allows organizations to create a private network by utilizing the public network. The network service authenticates an encrypted service credential using the SRVTAB to decrypt it. A credential issued by the KDC to authenticated users. The AAA framework uses a set of three independent security functions in a modular format to offer secure access control. Examples of biometrics include finger prints, face recognition, and DNA. In addition, DIAMETER also provides an improved method of encrypting message exchanges that offer more security than that provided by RADIUS. TACACS+ RESPONSE messages are sent by the server and contain one of the following: PASS_ADD (indicates that request is authorized), PASS_REPL ( sent by the AAA server when it ignores the request), FOLLOW ( the AAA wants to have Authorization performed on another server), ERROR (indicates indicate an error on the AAA server), TACACS+ Accounting also uses REQUEST and the RESPONSE messages, TACACS+ Accounting takes place by sending a record to the AAA server. There are two types of messages that are exchanged during RADUIS Accounting sessions: Accounting-Request and Accounting-Response messages. Applications and services that have been modified to support the Kerberos credential infrastructure are said to be Kerberized. The principal difference between RADIUS and TACACS+ mostly revolves around the way that TACACS+ both packages and implements AAA. It is important to remember that, depending on the Cisco IOS version your NAS is running, these commands can be performed on a single line or they may need to be implemented on a line-by-line basis. This keyword is used to specify the IP address of the hostname of a server in the group. This keyword is used to specify RADIUS IP parameters. Ans: Firstly let's know little bit Unlike RADIUS and TACACS+, Kerberos uses both TCP and UDP ports. In addition, DIAMETER is an AAA protocol that is designed to It provides greater granular control (than RADIUS) as the commands that are authorized to be used by the user can be specified. RADIUS server configuration has the following options: R1(config)#radius-server host 10.1.1.254 ?
WebRADIUS uses the UDP protocol while TACACS+ uses the TCP protocol. > Please consider CompTIA Security+ or Cisco CyberOps Associate. > The remote user then enters his or her credentials, providing the username iinsuser (which is the ATTRIBUTE) and password ccn@secur!ty (which is the VALUE for that ATTRIBUTE), as illustrated in step 3.
TACACS+ Accounting is similar to Authorization in that it uses the same two messages that Authorization uses, i.e.
Scalability. login Set authentication lists for logins. The keywords that fall within the scope of the IINS course requirements are described in the following table: The following example illustrates how to configure a TACACS+ server group named IINS-TACACS. Scalability numbers are likely to go up and these are some advantages for large customers. the services available to the user. WebQ Compare the relative merits of TACACS+ and RADIUS AAA servers.What advantages and disadvantages does each type of AAA server have? In addition to the standard set of attributes, RADIUS also specifies the vendor-specific attribute (Attribute 26) that allows vendors to support their own extended attributes, which may be specifically tailored to their particular application and are not for general use. RADIUS also offers this capability to some extent, but it's not as granular on Cisco devices; on some other vendors, this restriction is less limited. Pearson collects name, contact information and other information specified on the entry form for the contest or drawing to conduct the contest or drawing. AAA uses standard authentication methods, which Although firewall (e.g. If a single administrator wants to access 100 routers and the local database of the device is used for username and password (authentication) then the administrator has to make the same user account at different times. Accounting is illustrated in the following diagram: Based on the diagram above, in step 1, the remote user dials in to the NAS for access to the network resources and services. They need to be able to implement policies to determine who can log in to As identity security and access management become more complex, networks and network resources require safeguarding from unauthorized access.