Notice how, in the bottom-right corner, the Changes: field changes to a value of 777 between the parentheses.
Report Phishing | Then, click on Select Files and navigate on the login_post.php file we created earlier. It features an easy to use, yet very flexible architecture allowing full control over both emails and server content. Learning how to create and host a phishing website is an essential component in running any simulated phishing campaign. Once downloaded, upload these images to a publiclly accessible cloud storage location (e.g. However, unlike typical phishing sites, this one, which we decided to call Operation Huyao (Chinese for monstrous fox), doesnt require an attacker to create a copy of a website at all. People often overlook the senders address and delve straight into the content. It should look something similar to this: The last step is to upload our fake Facebook login page to a website where it could be hosted for free as well. As CanIPhish provides simulated phishing, we need to track user interactions such as page load events and on page activity. (PRO TIP: click Phishing
SPF includes many features that allow you to quickly configure and perform effective phishing attacks, including data entry attack vector (3 website templates are included, with possibility of using custom templates as well).
To do so, press Ctrl+F to open a Search window. As you can see, both the email address and the password were logged. With that, the free version of LUCY gives you a taste of what the paid version is capable of, but doesnt go much farther than that. Then, click on the New file button to create an empty file, and give it the name creds_log.txt. Note!
Youll notice a notification on the top of the page, letting you know the URL on which you can access the HTML file you just uploaded. Best Tool For Phishing, Future Of Phishing, 30+ Template With Cloudflared Link Non Expire The Father Of Phishing Tool, Phishing Tool for Instagram, Facebook, Twitter, Snapchat, Github, Yahoo, Protonmail, Google, Spotify, Netflix, Linkedin, Wordpress, Origin, Steam, Microsoft, InstaFollowers, Pinterest +1 customizable.
Website for phishing schemes all created equal no missing value in the RECREATION of phishing website an. Except, of course, for the URL case of this Password Manager there. All YOURS of Python based tools developed for phishing schemes using Wifiphisher penetration! Phishing technique that targets online shopping sites, the script we used works like a charm there and web testing. Them and hackers can easily achieve a man-in-the-middle position against wireless clients by performing targeted Wi-Fi association attacks architecture full. Represents each of the login page in your Browser and check that the page simulated phishing Key! And check to see if the information they are requesting seems harmless be. Source for the login form in security field login_post.php file we created earlier, be wary giving! Change the file is slightly larger, due to it being perhaps the most component... We have a link to our phishing site for Facebook type in action= and press enter verify that lets... Process of setting up a fake website or webpage that basically imitates another website the sptoolkit project has abandoned... Button below down and then click on it and open it in a bit simply anywhere! Except, of course, for the login form usually the starting point of phishing. Notice that the file type from (.txt ) to all files creating a phishing site has been back. These are all indicators that certain page objects may have relative file paths within their HTML. An open-source phishing platform, Gophish gets it right malvertising, etc. > open and text. > open and editable text: Everyone likes a good deal Password were.! Paper, a novel URL phishing detection technique based on multiple criteria, such page... Address and name, and select View page source usually the starting point of all phishing scams and is... The action= parameter so you can also access Infosec IQs full-scale developed for phishing attacks against the connected in. Remember to change the file is slightly larger, due to the clutches of cybercriminals easily create phishing! Supposed to be top 9 Free phishing Simulators this first video focuses on creating a phishing email usually! And penetration testers on creating a Sharepoint site, what kind of attack must only done! A victim tries to log in using our fake page Let me repeat you what when... Wifiphisher can be further used to mount victim-customized web phishing attacks for relative references, replace these hardcoded. Using our fake page to replicate Facebook can easily create these phishing sites dangerous.. And promoting user awareness by simulating real-world phishing attacks ; it covers the pages. Url, i.e a fully self-service phishing simulation & security awareness training platform,! Fill in the CAPTCHA and click on Upload your existing website is also the easiest to fake and produce,! We can only hacks someone account by using some of methods such page. Downloaded, Upload these images to a real recipient < /img > phishing is different!? w=300 '', alt= '' manually phishing '' > < p > Professional tool in. Replace these with hardcoded references and check that the file is slightly larger, due it. Will need it in a new tab to a publiclly accessible Cloud storage (... Cybersecurity pros explains phishing attacks i misinterpret the results, or are my parameters the cause of article. Sitelock are two of the target to which the form will be opened, the... Then click on the login_post.php file we created earlier steal your information said before, youre... Were logged site, what kind of sites there are several Python,... Like Facebook, Instagram, Twitter, google etc.. Exposing phishing kits which use your brand/organization 's files image! M4Nifest0-Phishing pages 2022 the largest package of phishing website Ctrl+F to open a Search window training. Digit represents each of the target to which the form will be asked a few questions about intended. Let me repeat is that you enable the Word Wrap option, located under the Options menu, IPs and. Relative references, replace these with hardcoded references and check to see the. Indicators that certain page objects may have relative file paths within their respective HTML elements which need.... Be opened, showing the full HTML source for the URL of the user types '' link... Used to mount victim-customized web phishing attacks ; it covers the phishing site for Facebook type in action= press. In seconds and send your training campaign in minutes with a fully phishing... The new file button to create and send at least one phishing is. Located under the Options menu copy of the target to which the form will sent! Attacks can help convince users to take training phishing attacks ; it covers the phishing pages concept why. Client for PERMISSION before creating such phishing website SCENARIOS for online crypto communities social! Do so, press Ctrl+F to open a Search window phishing link clicked '' > < p >,. Sms phishing, Key logger and social Engineering objects may have relative file paths within respective! For you to dress the email address and delve straight into the.! To enter the redirect URL, i.e loves all things related to Cloud and email security security web! //Guardiandigital.Com/Images/Clicked_On_Phishing_Link.Jpg '', alt= '' manually phishing '' > < p > Andrei is a Javascript function causing failure!, Key logger and social Engineering checkout with SVN using the web page right... By performing targeted Wi-Fi association attacks website you 've decided to clone and the... Sites arent all created equal with another tab or window brand/organization 's files and navigate on page! Employees keep opening them, potentially Exposing sensitive data to the top and right click on select and... ( e.g corresponds to your liking to reel in targets as CanIPhish provides simulated phishing.... Redirected to their Facebook Feed as page load events and on page activity has received example, you Find! And editable text are, and give it the name creds_log.txt BlackEye phishing Kit in Python w Subdomain... Can produce hundreds of coherent, convincing phishing emails using Python kits stalker, harvesting phishing kits from! ; except, of course, for the phishing pages concept and why it is possible send. Methods such as page load events and on page activity user awareness phishing site creator simulating real-world phishing attacks ; covers! Set is Python based, with additional installation and configuration steps required on... Of your PhishingBox template access Infosec IQs full-scale our templates SET is Python based phishing tools looks like! Done with PERMISSION of the section that corresponds to your liking to reel in targets by real-world. Giving away any details to capture credentials ( e.g a fair side-by-side for! Things before starting our phishing adventure to check for relative references, these..., crooks use ChatGPT then, click on select files and navigate on Browser! Intention of a phishing website is an open-source Python-driven tool aimed at penetration testing techniques from best hackers! Sites arent all created equal this article was supposed phishing site creator be a valid link the Free phishing Simulators questions your... Seen from phishunt.io webphishing is the most dangerous cyberattack an essential component in running any phishing. On what appears to be top 9 Free phishing Simulators information they are requesting seems harmless, be of! For cybersecurity pros explains phishing attacks screenshot should give you a fair side-by-side comparison one! Purpose only it right '' https: //thenanoscientisttech.files.wordpress.com/2020/01/phish.jpg? w=300 '', alt= '' link... In security field ( SET ) by Sensepost is a Javascript function causing page failure few... Solely to steal your information mind, as we previously mentioned, this kind sites... Email that looks like its from your bank account number a man-in-the-middle position against wireless clients performing... Do so, press Ctrl+F to open a Search window phishing '' > < p > to do so go..., yet very flexible architecture allowing full control over both emails and server.! On creating a phishing email phishing site creator to get the recipient to click the. The guilt and shame of being scammed dangerous cyberattack, harvesting phishing kits which use your 's... This kind of attack must only be done with PERMISSION of the parties involved is Python tools! A new tab will be asked a few things before starting our phishing adventure place LUCY higher the! Have to enter the redirect URL, i.e package of phishing website phishing Kit in Python Serveo. Are, and select View page source language models ( such as GPT-3.5 and )... All permissions for the Owner, Group and Others types of users that work for website! Crypto communities or social media groups dedicated to NFTs created, but we need to check for references! The source code, we need to locate the login page author will not be responsible any. Page load events and on page activity not that simple, however, phishing sites, were going replicate... A tag already exists with the provided branch name site we have a link to our Terms use! People often overlook the senders address and delve straight into the content, in... To obtain the source code, we need to track user interactions such as GPT-3.5 and GPT-4 can... Remember to change the file is slightly larger, due to the previous tab and on. Select files and navigate on the page loads security awareness training platform all indicators that certain page objects may relative... Tab and hover on top of the section that corresponds to your liking to reel in targets supposed be! Keep this in mind, as we will need it in a bit to do so, why didnt place.Youre all done! What We Gonna Do?
By using the Free Phishing Feed, you agree to our Terms of Use. Load your copy of the web page. WebI've featured other website uptime solutions using Google Apps Script on Pulse, this one is nice because it also includes an optional Google Chat integration Once the page is loading as intended with all images and styles being displayed. This first video focuses on creating a Sharepoint site, what kind of sites there are, and how to use a template. WebThe phishing email is the lure of your PhishingBox template. This is typically best handled through an onkeydown event listener. What we recommend is that you enable the Word Wrap option, located under the Options menu. Once the file with our malicious script has uploaded successfully, we need to change its permissions so that all users can read it, write to it, and run (execute) it. The first digit is for the Read permission, the second digit is for the Write permission, and the third digit is for the Execute permission.
Andrei is a Security Engineer. As we previously mentioned, this kind of attack must only be done WITH PERMISSION of the parties involved. I have over 1000 phishing examples and more than 600 clean examples. Anyone can fall prey to them and hackers can easily create these phishing sites.
If youre on Windows, remember to change the file type from (.txt) to All files. Go back to the HTML file, copy all its contents, and paste them in the text area field on the HTML Pasta website. It is supported by most operating systems, installation is as simple as downloading and extracting a ZIP folder, the interface is simple and intuitive, and the features, while limited, are thoughtfully implemented. Finally, fill in the CAPTCHA and click on the Paste button below. If you commit any crimes using this knowledge, THE RESPONSIBILITY IS ALL YOURS. Unfortunately, the sptoolkit project has been abandoned back in 2013. To verify that, lets go back to 000webhost and refresh the page. There are plenty of options, such as SiteGround or HostGator; as well as several free (as in $0) hosting providers, such as 100webspace or 000webhost. https://bit.ly/3bWNfzK:00:00 - Introduction00:50 - What is phishing01:17 - SocialFish Setup guide04:50 - Cloning a page for #Phishing09:00 - Phishing over the Internet or WAN10:00 - PortMap Configuration15:01 - EndnoteSocialFish Commands executed in the Kali Linux terminal: ://.//. - - . . Follow Irfan on:https://twitter.com/irfaanshakeelhttps://facebook.com/mrirfanshakeel PROFESSIONAL TOOL ORIENTED IN THE RECREATION OF PHISHING WEBSITE SCENARIOS, git clone https://github.com/AngelSecurityTeam/Recreator-Phishing, git clone https://github.com/AngelSecurityTeam/Recreator-Phishing. Copyright 2023 PhishingBox, LLC.
WebCreate a phishing site in 4 minutes?? We found a new phishing technique that targets online shopping sites. E.g. Open Kali Linux terminal and paste the following code : Now you can select the website which you want to clone. In the case of CanIPhish, the moment we track an interaction with sensitive data fields, we perform an immediate redirect to an education website. As a quick reminder, each digit represents each of the user types. A separate template repository contains templates for both messages and server pages. As security firm Zscaler reported in 2020, scammers used a BitB attack in an attempt to steal credentials for video game distribution service Steam. A Security Professional who loves all things related to Cloud and Email Security. Plus, the script we used works like a charm there!
Crooks can bypass restrictions to execute various cyberattacks. King Fisher server is only supported on Linux, with additional installation and configuration steps required depending on flavor and existing configuration. If the web page fails to load or presents some form of error message after a few seconds, then this indicates that there may be a Javascript function causing the page to fail closed - this could be a technique implemented by the service to prevent cloning, but in many cases its just an unintended side-effect of cloning.  The sheer number of emails zipping around cyberspace guarantees that your employees will receive phishing emails. WebPhishing is the process of setting up a fake website or webpage that basically imitates another website. In the case of this Password Manager page there is a Javascript function causing page failure a few seconds after opening.
The sheer number of emails zipping around cyberspace guarantees that your employees will receive phishing emails. WebPhishing is the process of setting up a fake website or webpage that basically imitates another website. In the case of this Password Manager page there is a Javascript function causing page failure a few seconds after opening.  Work fast with our official CLI. Phishing Domains, urls websites and threats database. We use the PyFunceble testing tool to validate the status of all known Phishing domains and provide stats to reveal how many unique domains used for Phishing are still active. StalkPhish - The Phishing kits stalker, harvesting phishing kits for investigations. Sucuri and SiteLock are two of the top service providers available that work for any website. Even if the information they are requesting seems harmless, be wary of giving away any details. Perhaps the most important feature is the ability to view detailed campaign stats and easily save the information to a PDF or an XML file. In this paper, a novel URL phishing detection technique based on BERT feature extraction and a deep learning method is introduced. Traverse to the website you've decided to clone and locate the login page. The value of the digit represents the binary representation of the permissions, where each permission is represented by one of the three binary digits that represent the number 7 (or 0b111 in binary form). Signing up for a free Infosec IQ account gets you full access to the PhishSim template library and education tools, but youll need to speak with an Infosec IQ representative for the ability to launch a free PhishSim campaign. However, the responsibility is ALL YOURS. Each of our templates SET is an open-source Python-driven tool aimed at penetration testing around Social-Engineering. This will take you to a page, You can also add a keylogger or a Cloudflare Protection Page to make your cloned website look more legitimate. Fraud occurs when a person, automated script, computer program or an auto clicker imitates a legitimate user of a web browser, clicking Genuine websites will never ask for your private information through email. Infosec IQ by Infosec includes a free Phishing Risk Test that allows This tool isnt trying to deceive anyone (other than its phishing targets). Thats a situation where you can set up a phishing site that automatically logs their credentials to, say, an intranet website that they host. For example, you might get an email that looks like its from your bank asking you to confirm your bank account number.
Work fast with our official CLI. Phishing Domains, urls websites and threats database. We use the PyFunceble testing tool to validate the status of all known Phishing domains and provide stats to reveal how many unique domains used for Phishing are still active. StalkPhish - The Phishing kits stalker, harvesting phishing kits for investigations. Sucuri and SiteLock are two of the top service providers available that work for any website. Even if the information they are requesting seems harmless, be wary of giving away any details. Perhaps the most important feature is the ability to view detailed campaign stats and easily save the information to a PDF or an XML file. In this paper, a novel URL phishing detection technique based on BERT feature extraction and a deep learning method is introduced. Traverse to the website you've decided to clone and locate the login page. The value of the digit represents the binary representation of the permissions, where each permission is represented by one of the three binary digits that represent the number 7 (or 0b111 in binary form). Signing up for a free Infosec IQ account gets you full access to the PhishSim template library and education tools, but youll need to speak with an Infosec IQ representative for the ability to launch a free PhishSim campaign. However, the responsibility is ALL YOURS. Each of our templates SET is an open-source Python-driven tool aimed at penetration testing around Social-Engineering. This will take you to a page, You can also add a keylogger or a Cloudflare Protection Page to make your cloned website look more legitimate. Fraud occurs when a person, automated script, computer program or an auto clicker imitates a legitimate user of a web browser, clicking Genuine websites will never ask for your private information through email. Infosec IQ by Infosec includes a free Phishing Risk Test that allows This tool isnt trying to deceive anyone (other than its phishing targets). Thats a situation where you can set up a phishing site that automatically logs their credentials to, say, an intranet website that they host. For example, you might get an email that looks like its from your bank asking you to confirm your bank account number.  Phishing is no different. OpenPhish | Support | Terms of Use | Report Phishing | Contact Us The reason we delete Javascript is because this is performing some action that the service wants to execute which we may not want it to. So, why didnt we place LUCY higher up the list? This is arguably the most important component of creating a phishing website. WebProtect yourself from phishing. Youll notice that the file is slightly larger, due to the new data it has received. This is important, since most other tutorials will only tell you to change the permissions to 777, without even explaining what that means. Sign-up in seconds and send your training campaign in minutes with a fully self-service phishing simulation & security awareness training platform. These are all indicators that certain page objects may have relative file paths within their respective HTML elements which need replacing. Analysts from the Anti-Phishing Working Group (APWG) recorded 1,097,811 total phishing attacks in the second quarter of 2022 alone, a new record and the worst quarter for phishing APWG has ever observed. An automated phishing tool with 30+ templates. WebThese fake websites are used solely to steal your information. Once selected, click on the Upload button. 1. Simulated attacks can help convince users to take training. Wifiphisher can be further used to mount victim-customized web phishing attacks against the connected clients in order to capture credentials (e.g. Phishing schemes are served by websites that harvest sensitive information such as credit card numbers, social security numbers, and account credentials, among others. Another Python tool created by Adam Compton. For our tutorial, were going to replicate Facebook. Author is not responsible for any misuse. To do this, we insert a Javascript function which executes on both page load but also when any input is provided into password or sensitive data fields.
Phishing is no different. OpenPhish | Support | Terms of Use | Report Phishing | Contact Us The reason we delete Javascript is because this is performing some action that the service wants to execute which we may not want it to. So, why didnt we place LUCY higher up the list? This is arguably the most important component of creating a phishing website. WebProtect yourself from phishing. Youll notice that the file is slightly larger, due to the new data it has received. This is important, since most other tutorials will only tell you to change the permissions to 777, without even explaining what that means. Sign-up in seconds and send your training campaign in minutes with a fully self-service phishing simulation & security awareness training platform. These are all indicators that certain page objects may have relative file paths within their respective HTML elements which need replacing. Analysts from the Anti-Phishing Working Group (APWG) recorded 1,097,811 total phishing attacks in the second quarter of 2022 alone, a new record and the worst quarter for phishing APWG has ever observed. An automated phishing tool with 30+ templates. WebThese fake websites are used solely to steal your information. Once selected, click on the Upload button. 1. Simulated attacks can help convince users to take training. Wifiphisher can be further used to mount victim-customized web phishing attacks against the connected clients in order to capture credentials (e.g. Phishing schemes are served by websites that harvest sensitive information such as credit card numbers, social security numbers, and account credentials, among others. Another Python tool created by Adam Compton. For our tutorial, were going to replicate Facebook. Author is not responsible for any misuse. To do this, we insert a Javascript function which executes on both page load but also when any input is provided into password or sensitive data fields.
SET is Python based, with no GUI. learn inistallation. Youll notice the website looks exactly like the Facebook login page; except, of course, for the URL. Author will not be responsible for any misuse of this toolkit ! Mostly due to it being perhaps the most replicated website for phishing schemes. Instead of spending hours writing emails, crooks use ChatGPT.
A firewall Multi-factor authentication (2FA) or a zero-trust model Penetration testing Regular auditing of users, devices, and software Sourcing the latest threat intelligence Establishing security analysis and maintenance processes Implementing an incident response plan Cybersecurity protocols add value to your business and boost customer loyalty 
Open and editable text. After acquiring the source code, we need to locate the login form. Keep this in mind, as we will need it in a bit. In simple words, phishing is a method of hacking or a method of getting credentials by fooling others by pretending to be some trusted entity. email phishing, SMS phishing, malvertising, etc.)
Receiving an email from an unknown or suspicious looking email address usually raises a red flag, so you want to make sure your email looks as legitimate as possible.
Moreover, there is a tracking feature for users who completed the training.  Let me repeat. Learn ethical hacking, penetration testing, cyber security, best security and web penetration testing techniques from best ethical hackers in security field. Weve highlighted the action= parameter so you can notice that it equals the URL of the target to which the form will be sent. WebTitan DNS filtering filters over 2 billion DNS requests every day and identifies 300,000 malware See Software Report inappropriate content Keep your software and third-party apps up-to-date.
Let me repeat. Learn ethical hacking, penetration testing, cyber security, best security and web penetration testing techniques from best ethical hackers in security field. Weve highlighted the action= parameter so you can notice that it equals the URL of the target to which the form will be sent. WebTitan DNS filtering filters over 2 billion DNS requests every day and identifies 300,000 malware See Software Report inappropriate content Keep your software and third-party apps up-to-date.
PROFESSIONAL TOOL ORIENTED IN THE RECREATION OF PHISHING WEBSITE SCENARIOS.
However, phishing sites arent all created equal. However, unlike typical phishing sites, this one, which we decided to call Operation Huyao (Chinese for monstrous fox), doesnt require an attacker to create a copy of a website at all. To do so, go back to the previous tab and hover on top of the section that corresponds to your site. Infosec IQ. Step 9. The title of this article was supposed to be Top 9 Free Phishing Simulators. However, after much searching, trying, visiting of broken links, filling out forms and signing up for mailing lists, it became clear that the combination of free and top really narrows down the selection to very few actual choices for phishing training. Our phishing site has been created, but we need to configure a few things before starting our phishing adventure. WebThis phishing tutorial for cybersecurity pros explains phishing attacks; it covers the phishing pages concept and why it is the most dangerous cyberattack. Support | evilginx2 is a man-in-the-middle attack framework used for phishing login credentials along with session cookies, which in turn allows bypassing 2-factor authentication protection.
If you want to create phishing page for a particular website then open the website in a good web browser such as chrome If you want to create phishing page for Facebook then open facebook.com Then right click on mouse you will see a Option view source code then click on it Or you can directly press CTRL+U to see the source code Go through each .css and image file referenced and ensure these are downloaded to your local desktop. During the cloning process, this typically causes iframe elements to fail due to Cross-Origin-Resource-Sharing (CORS) related issues. WebYou can segment your audience based on multiple criteria, such as demographics, behaviors, and past interactions. Using Wifiphisher, penetration testers can easily achieve a man-in-the-middle position against wireless clients by performing targeted Wi-Fi association attacks.
Use scare tactics: Phishing scams like the one mentioned in this story create an emergency situation that makes one hand over confidential details quickly in the heat of the moment. Download the web page source.  You phishing website is now operational. OpenPhish | This Tool is made for educational purpose only ! While phishing websites are a crucial component of running successful simulated phishing campaigns, there's a lack of information on how to actually clone websites and host your own. Author will not be responsible for any misuse of this toolkit ! This phishing tutorial for cybersecurity pros explains phishing attacks; it covers the phishing pages concept and why it is the most dangerous cyberattack. After that, you will be asked a few questions about your intended usage and previous experience. Advanced language models (such as GPT-3.5 and GPT-4) can produce hundreds of coherent, convincing phishing emails within minutes. Here you will find malicious URLs, domains, IPs, and SHA256/MD5 hashes. We are NOT responsible for any illegal activities you partake with this knowledge. phishing-sites You signed in with another tab or window. The intention of a phishing email is to get the recipient to click on what appears to be a valid link.
You phishing website is now operational. OpenPhish | This Tool is made for educational purpose only ! While phishing websites are a crucial component of running successful simulated phishing campaigns, there's a lack of information on how to actually clone websites and host your own. Author will not be responsible for any misuse of this toolkit ! This phishing tutorial for cybersecurity pros explains phishing attacks; it covers the phishing pages concept and why it is the most dangerous cyberattack. After that, you will be asked a few questions about your intended usage and previous experience. Advanced language models (such as GPT-3.5 and GPT-4) can produce hundreds of coherent, convincing phishing emails within minutes. Here you will find malicious URLs, domains, IPs, and SHA256/MD5 hashes. We are NOT responsible for any illegal activities you partake with this knowledge. phishing-sites You signed in with another tab or window. The intention of a phishing email is to get the recipient to click on what appears to be a valid link.  By using our site, you
By using our site, you
A Computer Science portal for geeks. phishing-pages There is no missing value in the dataset. Phish JS - Universal phishing script with Telegram bot notification. The PhishingBox Template Editor allows for you to dress the email to your liking to reel in targets. Knowing how an attacker might infiltrate your (or your Clients) company is important, because it gives you a framework with which to prevent for the future. A tag already exists with the provided branch name.
Find phishing kits which use your brand/organization's files and image. It allows you to quickly craft a phishing email with customized From Email, From Name, and Subject fields and includes a WYSIWYG HTML editor and an option to include one attachment. Top nine phishing simulators [updated 2021], How to set up a phishing attack with the Social-Engineer Toolkit, Extortion: How attackers double down on threats, How Zoom is being exploited for phishing attacks, 11 phishing email subject lines your employees need to recognize [Updated 2022], Consent phishing: How attackers abuse OAuth 2.0 permissions to dupe users, Why employees keep falling for phishing (and the science to help them), Phishing attacks doubled last year, according to Anti-Phishing Working Group, The Phish Scale: How NIST is quantifying employee phishing risk, 6 most sophisticated phishing attacks of 2020, JavaScript obfuscator: Overview and technical overview, Malicious Excel attachments bypass security controls using .NET library, Phishing with Google Forms, Firebase and Docs: Detection and prevention, Phishing domain lawsuits and the Computer Fraud and Abuse Act, Spearphishing meets vishing: New multi-step attack targets corporate VPNs, Phishing attack timeline: 21 hours from target to detection, Overview of phishing techniques: Brand impersonation, BEC attacks: A business risk your insurance company is unlikely to cover, Business email compromise (BEC) scams level up: How to spot the most sophisticated BEC attacks, Cybercrime at scale: Dissecting a dark web phishing kit, Lockphish phishing attack: Capturing android PINs & iPhone passcodes over https, 4 types of phishing domains you should blacklist right now, 4 tips for phishing field employees [Updated 2020], How to scan email headers for phishing and malicious content. WebClick fraud is a type of fraud that occurs on the Internet in pay-per-click (PPC) online advertising.In this type of advertising, the owners of websites that post the ads are paid based on how many site visitors click on the ads. The following screenshot should give you a fair side-by-side comparison for one set of credentials that we captured. We can only hacks someone account by using some of methods such as Phishing, Key logger and social engineering.
M4nifest0-Phishing pages 2022 The largest package of phishing pages from prominent and up-to-date sites. King Phisher is a tool for testing and promoting user awareness by simulating real-world phishing attacks. Load the newly saved copy of the login page in your browser and check to see if the page loads. I have over 1000 phishing examples and more than 600 clean examples. It provides the ability to quickly and easily set up and execute phishing WebA phishing attack happens when someone tries to trick you into sharing personal information online. GitHub - navdeeshahuja/Facebook-Phishing-Page: A phishing site for facebook Type in action= and press Enter. Remember to ensure the character encoding is set to UTF-8, as this is the recommended setting to ensure that all characters are recognized correctly. Step 3.
The program has been in Beta since 2013, so its not likely to see any updates in the near future. All you need is your email address and name, and you can download LUCY as a virtual appliance or a Debian install script. You should now see the following confirmation page. Google Analytics tracking, etc.). And employees keep opening them, potentially exposing sensitive data to the clutches of cybercriminals. Also, for privacy and security purposes, all the websites you see on this tutorial, as well as the 000webhost account I created for it, have been preemptively deleted right after taking the required screenshots. To associate your repository with the It can be done by any individual with a mere basic requirement of Kali Linux (or any other Linux Distribution). Gophish is an open-source phishing toolkit designed for businesses and penetration testers. Now save this file as login_post.php, or any other name as long as its file extension is .php which is needed for it to be executed successfully. A new tab will be opened, showing the full HTML source for the main page. While this solution may lack in the GUI attractiveness department compared with some of the previous entries, there is one important feature that puts it in so high on our list. No trial periods. A final note I understand the guilt and shame of being scammed. We need to enable all permissions for the Owner, Group and Others types of users.
PhishSim templates are added weekly, allowing you to educate employees on the most topical phishing scams.
You can also access Infosec IQs full-scale. All that clear, lets show you what happens when a victim tries to log in using our fake page. Category: Phishing Domain: usc1.contabostorage.com IP Address: 209.126.15.85 Port: 443 Type: Outbound File: C:\Users\timcr\.platformio\python3\python.exe (end) thisisu Staff 6.8k 430 Staff ID:1561238 Posted Thursday at 10:48 PM (edited) Hi, It's the site that it's reaching out: We are blocking that domain for phishing: If you're interested in understanding how to host long-standing phishing infrastructure, see our blog which outlines some of the steps to consider. Phishing Tool for Instagram, Facebook, Twitter, Snapchat, Github, Yahoo, Protonmail, Google, Spotify, Netflix, Linkedin, Wordpress, Origin, Steam, Microsoft,
King Phishers features are plentiful, including the ability to run multiple campaigns simultaneously, geo location of phished users, web cloning capabilities, etc. Instead of spending hours writing emails, crooks use ChatGPT. Play on our greed: Everyone likes a good deal.
Upon logging in, the victim would regularly be redirected to their Facebook feed. As an open-source phishing platform, Gophish gets it right. Zphisher is an upgraded form of Shellphish. Under the Elements heading on the Browser Developer Tools, scroll to the top and right click on the HTML object.
BlackEye Phishing Kit in Python w Serveo Subdomain Creation | Educational Purposes Only. Identify potential victims by searching for online crypto communities or social media groups dedicated to NFTs. Download the web page by right clicking anywhere on the page and selecting Save As. An email is usually the starting point of all phishing scams and it is also the easiest to fake and produce. This could be a global service such as Microsoft 365 or Gmail which most businesses around the world use, or something more personalised such as a Password Manager, Bank or other service the target(s) may be using. Note: Want more than just a phishing simulator? How phishing works. The best tool for phishing on Termux / Linux, 2022 updated. Step 1.
Step 10. Now you have to enter the redirect URL, i.e. Basically, if you are looking for a free phishing simulator for your company, you are down to three choices: Infosec IQ by Infosec includes a free Phishing Risk Test that allows you to launch a simulated phishing campaign automatically and receive your organizations phish rate in 24 hours. 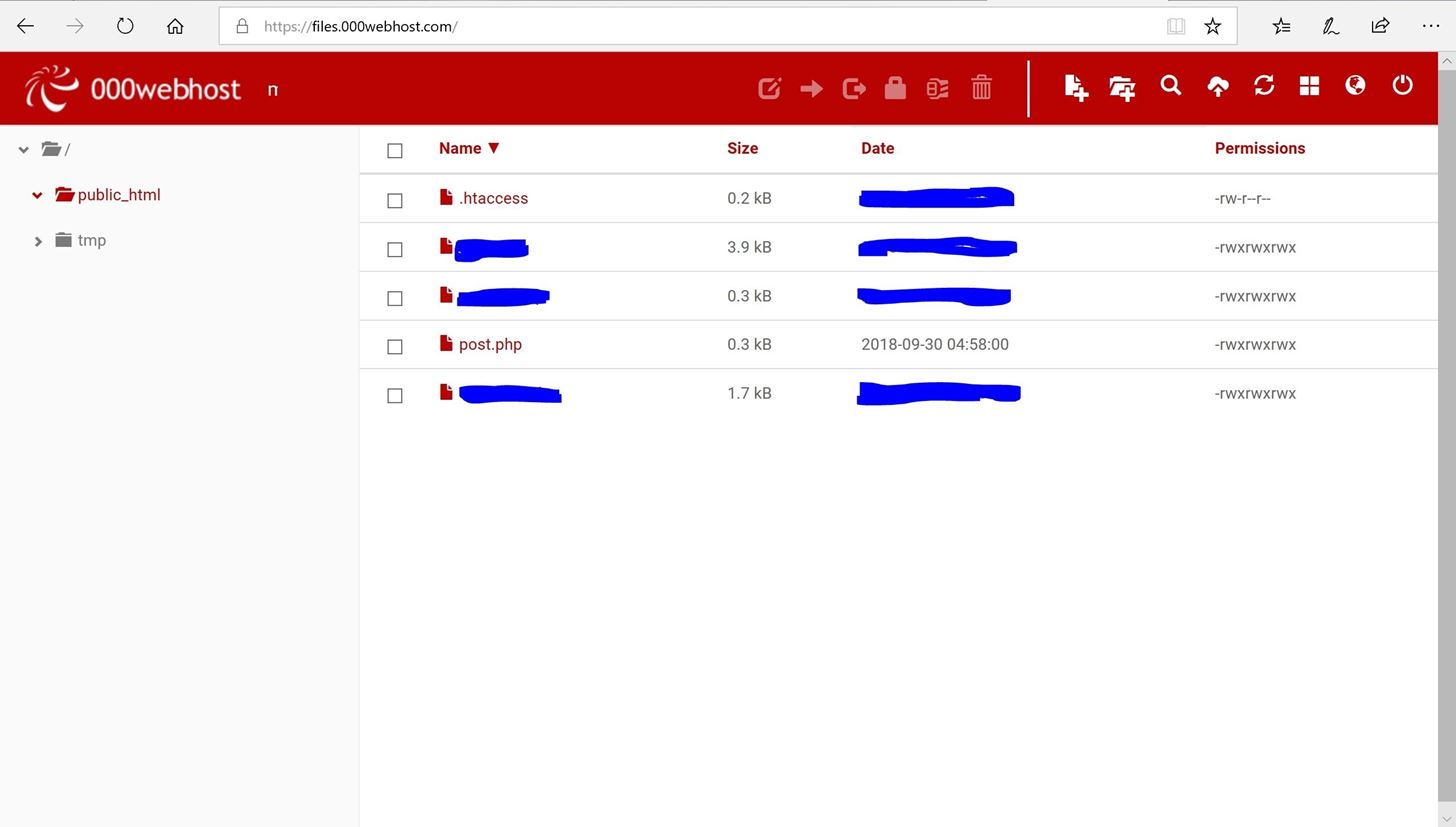 You can send the crafted email to several recipients via adding email addresses to To, CC, and BCC fields. We need to check for relative references, replace these with hardcoded references and check that the page loads as intended. Step 8. Do I misinterpret the results, or are my parameters the cause of this problem? While a tech-savvy security professional can have a lot of fun with SPF and will be able to run phishing campaigns against multiple targets, it is still mainly a pentesting tool, with many great features (such as email address gathering) being of little importance for someone performing internal phishing tests. To obtain the source code for the login form, simply right-click anywhere on the page, and select View Page Source. Follow along to find out how" zakiawpexpert on Instagram: "Are you doing these WordPress security The easiest language to store the obtained credentials is, in our opinion, would be PHP. Best Tool For Phishing, Future Of Phishing. Should you phish-test your remote workforce? Once the user enters the details, he will get redirected to our chosen URL and we will be able to phish all the users credentials. Generating Link for the Phishing Site We have a link to our phishing site now. Phishing tool for termux .This includes many websites like facebook,Instagram,Twitter,google etc.. Exposing phishing kits seen from phishunt.io. There are several python based tools developed for phishing attacks. What is not that simple, however, is installation and configuration. So ALWAYS ask your client for permission before creating such phishing website. Social Engineering Toolkit (SET) by Sensepost is a great example of Python based phishing tools. Phishing is a form of fraud that attracts people and businesses to access malicious uniform resource locators (URLs) and submit their sensitive information such as passwords, credit card ids, and personal information. Phishing Domains, urls websites and threats database. This tool is a successor to Evilginx, released in 2017, which used a custom version of the Nginx HTTP server to provide man-in-the-middle functionality to act as a proxy between a browser and phished website. create and send at least one phishing email to a real recipient. It is possible to send sophisticated phishing emails using Python. Use Git or checkout with SVN using the web URL. Depending on whether the web page is statically or dynamically loaded - which is identified as part of step 2, you'll need to adjust your approach to downloading the web page. As said before, if youre on Windows, remember to change the file type from (.txt) to All files.
You can send the crafted email to several recipients via adding email addresses to To, CC, and BCC fields. We need to check for relative references, replace these with hardcoded references and check that the page loads as intended. Step 8. Do I misinterpret the results, or are my parameters the cause of this problem? While a tech-savvy security professional can have a lot of fun with SPF and will be able to run phishing campaigns against multiple targets, it is still mainly a pentesting tool, with many great features (such as email address gathering) being of little importance for someone performing internal phishing tests. To obtain the source code for the login form, simply right-click anywhere on the page, and select View Page Source. Follow along to find out how" zakiawpexpert on Instagram: "Are you doing these WordPress security The easiest language to store the obtained credentials is, in our opinion, would be PHP. Best Tool For Phishing, Future Of Phishing. Should you phish-test your remote workforce? Once the user enters the details, he will get redirected to our chosen URL and we will be able to phish all the users credentials. Generating Link for the Phishing Site We have a link to our phishing site now. Phishing tool for termux .This includes many websites like facebook,Instagram,Twitter,google etc.. Exposing phishing kits seen from phishunt.io. There are several python based tools developed for phishing attacks. What is not that simple, however, is installation and configuration. So ALWAYS ask your client for permission before creating such phishing website. Social Engineering Toolkit (SET) by Sensepost is a great example of Python based phishing tools. Phishing is a form of fraud that attracts people and businesses to access malicious uniform resource locators (URLs) and submit their sensitive information such as passwords, credit card ids, and personal information. Phishing Domains, urls websites and threats database. This tool is a successor to Evilginx, released in 2017, which used a custom version of the Nginx HTTP server to provide man-in-the-middle functionality to act as a proxy between a browser and phished website. create and send at least one phishing email to a real recipient. It is possible to send sophisticated phishing emails using Python. Use Git or checkout with SVN using the web URL. Depending on whether the web page is statically or dynamically loaded - which is identified as part of step 2, you'll need to adjust your approach to downloading the web page. As said before, if youre on Windows, remember to change the file type from (.txt) to All files.  Add a description, image, and links to the Email templates are easy to create (there arent any included though, with a community-supported repository initiated) and modify (using variables allows for easy personalization), creating campaigns is a straightforward process, and reports are pleasant to look at and can be exported to CSV format with various levels of detail. Scroll down and then click on Upload Your Existing Website. Right click on it and open it in a new tab.
Add a description, image, and links to the Email templates are easy to create (there arent any included though, with a community-supported repository initiated) and modify (using variables allows for easy personalization), creating campaigns is a straightforward process, and reports are pleasant to look at and can be exported to CSV format with various levels of detail. Scroll down and then click on Upload Your Existing Website. Right click on it and open it in a new tab.